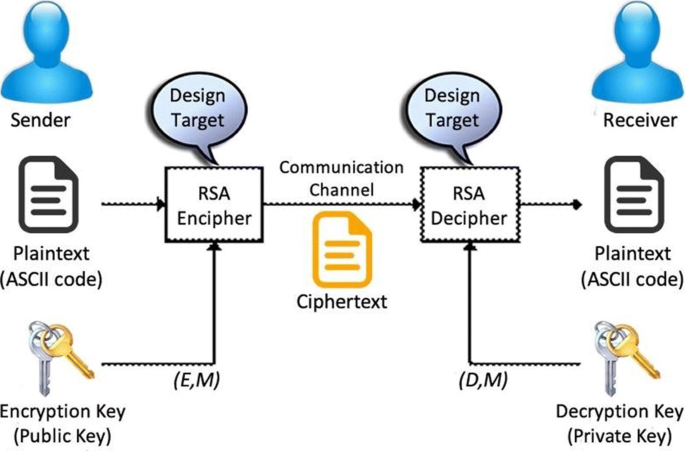
RSA [1] is an oldest partial homomorphic encryption approach. It is an asymmetric encrypted approach. It was built upon the hardness of prime factorization. Prime Factorization problem Finding the two factors or integers p and q > 1 such that pq = I with a given Composite integer I is known as factoring.Partially homomorphic encryption supports power operations as an extension of supporting multiplicative operations. For example, the RSA encryption algorithm is a multiplicatively homomorphic algorithm used by computers to encrypt and decrypt messages and is a form of public key cryptography.For example, say a user wants to upload data to a cloud-based server. They would be able to encrypt it, turning it into ciphertext, and upload it. The server would then process that data without decrypting it, and then the user would get it back. Only then would the user decrypt it with their secret key.
What are fully homomorphic encryption methods : Fully Homomorphic Encryption is the process of encrypting data in a way so that it never has to be decrypted for any processing done with that data. It is called FHE for short, because its a lot to say every time.
What type of encryption is RSA
RSA is a type of asymmetric encryption, which uses two different but linked keys. In RSA cryptography, both the public and the private keys can encrypt a message. The opposite key from the one used to encrypt a message is used to decrypt it.
What kind of encryption does RSA use : asymmetric encryption algorithm
The Rivest-Shamir-Adleman (RSA) encryption algorithm is an asymmetric encryption algorithm that is widely used in many products and services. Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data.
The HE can be categorized into three groups based on the number of mathematical operations on the encrypted message. They are: Partially Homomorphic Encryption (PHE), Somewhat Homomorphic Encryption (SHE) and Fully Homomorphic Encryption (FHE) as shown in Fig. 5.
RSA is a type of asymmetric encryption, which uses two different but linked keys. In RSA cryptography, both the public and the private keys can encrypt a message.
What is RSA algorithm in cryptography
Rivest Shamir Adleman (RSA) is a well-known public-key or asymmetric cryptographic algorithm. It protects sensitive data through encryption and decryption using a private and public key pair.Because RSA encryption is a deterministic encryption algorithm (i.e., has no random component) an attacker can successfully launch a chosen plaintext attack against the cryptosystem, by encrypting likely plaintexts under the public key and test if they are equal to the ciphertext.RSA typically refers to a public-key cryptosystem which is widely used for secure data transmission. It uses paired keys where one is used to encrypt messages and the other to decrypt them. RSA is therefore not a hash function. That said, algorithms that use RSA crypto keys often use hashes to sign messages.
There are two types of HE available in literature, partial homomorphic encryption (PHE) and fully homomorphic encryption (FHE).
What are the weakness of RSA encryption : Some of the weaknesses are due to the common modulus attack, the blinding attack, the small encryption exponent "e", the small decryption exponent "d", the forward search attack, timing attack, attack due to the multiplicative properties, the cycling attack, attack due to message concealing, the faulty encryption …
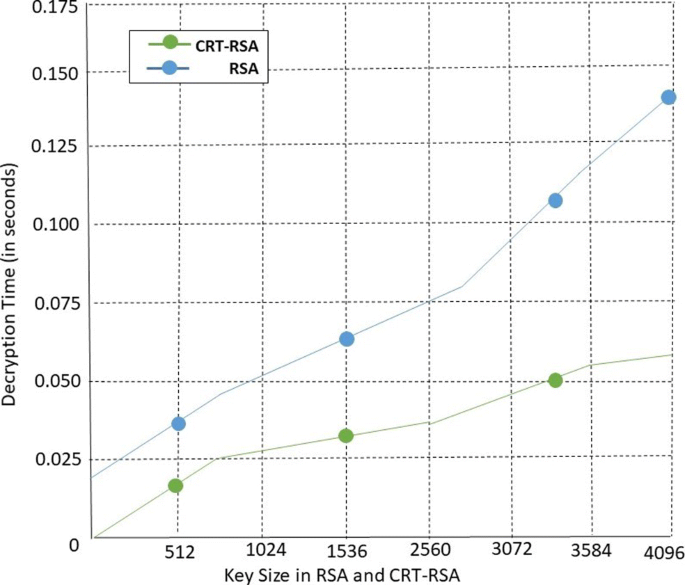
Is RSA encryption outdated : Cybersecurity experts consider 2048-bit encryption keys to be safe at least till 2030. RSA encryption keys have become very common in digital security to maintain data integrity and secure communications primarily.
What is the difference between encryption and homomorphic encryption
Homomorphic encryption is simply more secure than traditional encryption schemes. Like traditional encryption, homomorphic encryption schemes use a public key to encrypt the data. Unlike traditional encryption, homomorphic cryptosystems use more complex mathematical algorithms to ensure the data cannot be hacked.
No, RSA Encryption Isn't Obsolete | American Enterprise Institute – AEI.RSA's public/private key pair creation method is susceptible to factorization attacks. In a factorization attack, an attacker impersonates a key owner and can get the private key for the pairing. This allows attackers to decrypt sensitive data and bypass a system's security.
What is replacing RSA : In the next 10 years, public-key encryption needs to be replaced by post-quantum techniques that can stand up to the new challenges. May 6, 2022.