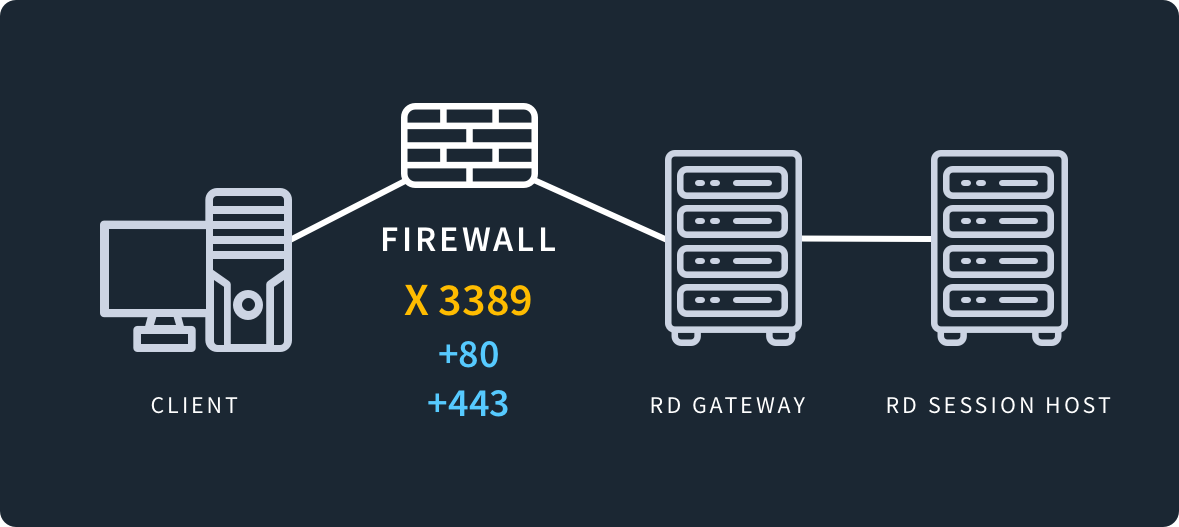
Having port 3389 open in your firewall can expose you to various security threats, such as man-in-the-middle attacks. Port 3389 is the default RDP port, making it an attractive target for hackers who know about its vulnerabilities. Never leave port 3389 exposed to the public Internet unless you cannot avoid it.To protect against port-based attacks: Lock down port 3389: Secure tunneling software can help stop attackers from sending requests that reach port 3389. With a secure tunnel (e.g. Cloudflare Tunnel) in place, any requests that do not pass through the tunnel will be blocked.When you connect to a computer (either a Windows client or Windows Server) through the Remote Desktop client, the Remote Desktop feature on your computer "hears" the connection request through a defined listening port (3389 by default). You can change that listening port on Windows computers by modifying the registry.
How can I tell if RDP port 3389 is open : Using Command Prompt (Windows):Open Command Prompt. Run the following command:arduinoCopy code netstat -an | find "3389" If the RDP port (3389 by default) is listening, you'll see an output with the local address followed by ":3389" in the "LISTENING" state.
Is it safe to open RDP port
Exposing an adequately-secured RDP port on the open internet isn't a guaranteed entry point for attackers into your network, but it is a high and unnecessary risk that.
Should ports be open or closed : The answer to this question depends on your specific security requirements and network configuration. In general, you should close ports that are not necessary for the normal operation of your system or network.
Common High-Risk Ports
| Port | Protocol | Recommended Action |
|---|---|---|
| 139 | TCP and UDP | Disable always. |
| 445 | TCP and UDP | Disable always. |
| 161 | TCP and UDP | Disable always. |
| 389 | TCP and UDP | Disable always. |
Remote Desktop Protocol (RDP) is a Microsoft proprietary protocol that enables remote connections to other computers, typically over TCP port 3389.
What is the vulnerability of port 3389
This vulnerability (listed as a feature by Microsoft) allows a remote attacker to view his victim's desktop without his consent, and even control it on demand, using tools native to the operating system itself.What is 3389 port used for It is used to allow users to connect to remote computers. For instance, Microsoft Remote Desktop Protocol typically uses TCP port 3389 to enable Remote Desktop connections to other computers.The default port used for Remote Desktop is TCP port 3389. This is the port that needs to be opened on the firewall and forwarded from the router to the computer hosting the Remote Desktop service. Opening this port enables remote access to the computer's graphical user interface (GUI) over a network connection.
Open ports aren't dangerous by default, rather it's what you do with the open ports at a system level, and what services and apps are exposed on those ports, that should prompt people to label them dangerous or not. The reason people call for closed ports because less open ports reduces your attack surface.
What ports are bad to have open : These are the ports most targeted by attackers:
- Ports 137 and 139 (NetBIOS over TCP) and 445 (SMB)
- Port 22 (SSH)
- Port 53 (DNS)
- Port 25 (SMTP)
- Port 3389 (remote desktop)
- Ports 80, 443, 8080 and 8443 (HTTP and HTTPS)
- Ports 20 and 21 (FTP)
- Port 23 (Telnet)
Is it OK to leave port 80 open : Summary. Opening port 80 on your firewall is no different than opening port 443, provided the web server is configured to redirect the traffic to a secure port. This also ensures users connecting on port 80 do not get connection errors.
What ports need to be opened for RDP
The default port used for Remote Desktop is TCP port 3389. This is the port that needs to be opened on the firewall and forwarded from the router to the computer hosting the Remote Desktop service. Opening this port enables remote access to the computer's graphical user interface (GUI) over a network connection.
Here's how:
- First, ensure that you've allowed the RDP port through the public network from Windows Firewall as described above.
- After logging in, navigate to the section where you can define traffic rules or port forwarding settings.
- Create a new rule or port forwarding entry.
- Specify the port as 3389.
Cybercriminals actively target port 3389. They even initiate automated scans across the internet to hunt for it. Once they identify you're using it, they will launch a range of attacks, like brute force attempts to exploit the port's known vulnerabilities.
What ports should never be open : Common High-Risk Ports
| Port | Protocol | Recommended Action |
|---|---|---|
| 25 | TCP | Disable always. Use SMTPS instead. |
| 110 | TCP | Disable always. Use POP3S instead. |
| 143 | TCP | Disable always. Use IMAPS instead. |
| 80, 8000, 8080, and 8888 | TCP | Disable recommended. Use HTTPS instead. |