
Homomorphic encryption can have higher computation times and limited calculation operations, which can impact its efficiency . Additionally, some homomorphic encryption schemes suffer from issues such as extensive memory storage and computing power requirements .Another challenge of homomorphic encryption is to ensure its security and correctness. Security means that the ciphertexts do not leak any information about the plaintexts, even to an adversary who can observe or manipulate the computations.Fully Homomorphic Encryption (FHE): This is the most powerful type of homomorphic encryption, allowing for arbitrary computations on encrypted data of any type. It is also the most computationally expensive and difficult to implement, which has been a major challenge for folks trying to use it in the real world.

What are the alternatives to homomorphic encryption : One of the most popular alternatives to homomorphic encryption is cryptography. Cryptography uses different methods to hide information, including microdots and scrambling text and images.
What is the weakest encryption method
33. Electronic Code Book (ECB). Electronic Code Book (ECB) is the simplest symmetric encryption scheme and also the weakest, producing a block of ciphertext for each block of plaintext.
What is the weakest encryption type : Data Encryption Standard
The DES (Data Encryption Standard) family is a symmetric block cipher. It was designed to handle only 56-bit keys which is not enough for modern computing power. It is now considered to be weak encryption.
Practicalities. Homomorphic encryption is very computationally intensive. Compared to processing the same data in clear, it is slower, less efficient, and more energy-consuming.
Craig Gentry, using lattice-based cryptography, described the first plausible construction for a fully homomorphic encryption scheme in 2009. Gentry's scheme supports both addition and multiplication operations on ciphertexts, from which it is possible to construct circuits for performing arbitrary computation.
Is homomorphic encryption used today
Today, homomorphic encryption can be used for more secure elections. Microsoft's ElectionGuard, for example, uses homomorphic encryption to ensure accurate voting results.Back in May of 2022 I transferred teams at Google to work on Fully Homomorphic Encryption (newsletter announcement). Since then I've been working on a variety of projects in the space, including being the primary maintainer on github.com/google/fully-homomorphic-encryption, which is an open source FHE compiler for C++.Answer. Explanation: WEP is the least secure type of encryption and should only be used if necessary. WPA and WPA2 are more secure, and WPA2 is the most secure type of encryption available.

one-time pad (OTP)
A stream cipher is designed based on the only completely unbreakable encryption algorithm: the one-time pad (OTP). The OTP takes a random secret key the same length as the plaintext and exclusive-ors (XORs) each bit of the plaintext and key together to produce the ciphertext as shown in the image above.
What is the hardest encryption to break : AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. While it is theoretically true that AES 256-bit encryption is harder to crack than AES 128-bit encryption, AES 128-bit encryption has never been cracked.
What are the 4 types of encryption : 11. What are the 4 basic types of encryption systems
- Advanced Encryption Standard (AES)
- Triple DES.
- Blowfish.
- Rivest-Shamir-Adleman (RSA)
Which is the slowest encryption algorithm
i- Figure 4 shows that the blowfish algorithm records the fastest encryption time, and RSA algorithm records the slowest encryption time.

DES
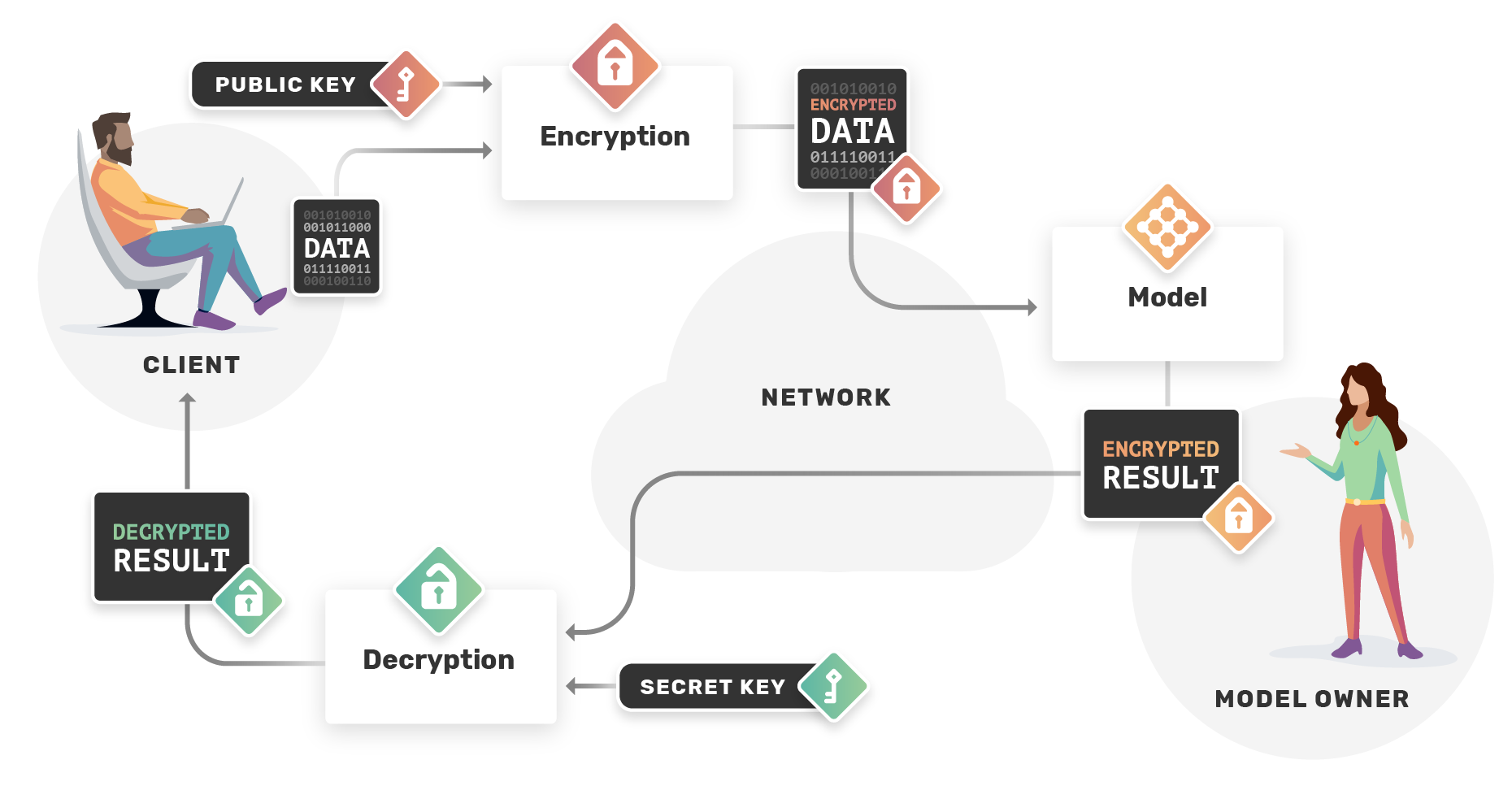
DES (Data Encryption Standard): is a symmetric key algorithm that uses a 56-bit key. It is considered weak because it can be cracked with a brute-force attack in a reasonable amount of time. RC4 (Rivest Cipher 4): is a stream cipher that was widely used in the 1990s and early 2000s.For example, say a user wants to upload data to a cloud-based server. They would be able to encrypt it, turning it into ciphertext, and upload it. The server would then process that data without decrypting it, and then the user would get it back. Only then would the user decrypt it with their secret key.
What is the weakest encryption : DES
DES (Data Encryption Standard): is a symmetric key algorithm that uses a 56-bit key. It is considered weak because it can be cracked with a brute-force attack in a reasonable amount of time. RC4 (Rivest Cipher 4): is a stream cipher that was widely used in the 1990s and early 2000s.



