
Homomorphic encryption can be either additive or multiplicative, while also being partially, somewhat or fully homomorphically encrypted: Partially homomorphic encryption. A defined operation can be performed infinite times on the ciphertext. These encryption schemes are relatively easy to design.The main difference between TFHE, BFV, and BGV on one side and CKKS on the other is that the first three perform calculations on integer numbers, while the CKKS scheme can perform calculations on float numbers. In TFHE operations are leveled and bootstrapped, but in CKKS, BGV and BFV operations are just leveled.Fully homomorphic encryption has many applications, including in the blockchain space. One key example is that can be used to implement privacy-preserving light clients (the light client hands the server an encrypted index i , the server computes and returns data[0] * (i = 0) + data[1] * (i = 1) + …
What is the homomorphic encryption technique : In practice, homomorphic encryption allows you to subdivide encrypted data so you have one key to decrypt the entire data set and several other keys that only decrypt the subparts. This gives you the opportunity to have different pieces of encrypted data to be worked on or viewed by different people independently.
Is RSA a homomorphic encryption
In fact, some common encryption algorithms are partially homomorphic by chance. For example, the RSA algorithm is multiplicatively homomorphic. The reason for this is that encryption in RSA is based on exponentiation: C = (m^x) (mod n) where m is the message and x is the secret key.
How many types of encryption are there : two types
There are two types of encryption in widespread use today: symmetric and asymmetric encryption.
The crucial difference between BGV and BFV is their plaintext encoding. As already suggested by Equations (1) and (2), the BGV scheme encodes the plain- text in the “least significant bits” of the ciphertext, whereas BFV uses the “most significant bits”.
Somewhat Homomorphic Encryption (SHE): In SHE, both addition and multiplication operation is allowed but with only a limited number of times. Fully Homomorphic Encryption (FHE): FHE allows a large number of different types of evaluation operations on the encrypted message with unlimited number of times.
What are the alternatives to homomorphic encryption
One of the most popular alternatives to homomorphic encryption is cryptography. Cryptography uses different methods to hide information, including microdots and scrambling text and images.Therefore, ECC homomorphic encryption method is used to protect the privacy of data, which effectively protects the privacy of users during data aggregation. What cloud center obtains is the final result of aggregation, and the privacy data of each user is unknown, which ensures the data security of users.The main components of an encryption system are: (1) plaintext (not encrypted message), (2) encryption algorithm (works like a locking mechanism to a safe), (3) key (works like the safe's combination), and (4) ciphertext (produced from plaintext message by encryption key).

Now let's look at seven common methods of encryption that you can use to safeguard sensitive data for your business.
- Advanced Encryption Standard (AES)
- Triple Data Encryption Standard (TDES)
- Rivest Shamir Adleman (RSA)
- Blowfish.
- Twofish.
- Format-Preserving Encryption (FPE)
- Elliptic Curve Cryptography (ECC)
Is BGV fully homomorphic : BGV was proposed by Zvika Brakerski, Craig Gentry and Vinod Vaikuntanathan and is a fully homomorphic encryption method. We encrypt a single bit at a time, and then fit into a circuit.
What is a BGV : Background verification or BGV is synonymous with employee verification. It is the process of ascertaining the identity and credentials of an individual for the purpose of hiring, loan giving, tenancy, marriage, etc. First impressions are often misleading and one must refrain from purely relying on a 'gut feeling'.
Is RSA partially homomorphic
RSA [1] is an oldest partial homomorphic encryption approach. It is an asymmetric encrypted approach. It was built upon the hardness of prime factorization. Prime Factorization problem Finding the two factors or integers p and q > 1 such that pq = I with a given Composite integer I is known as factoring.
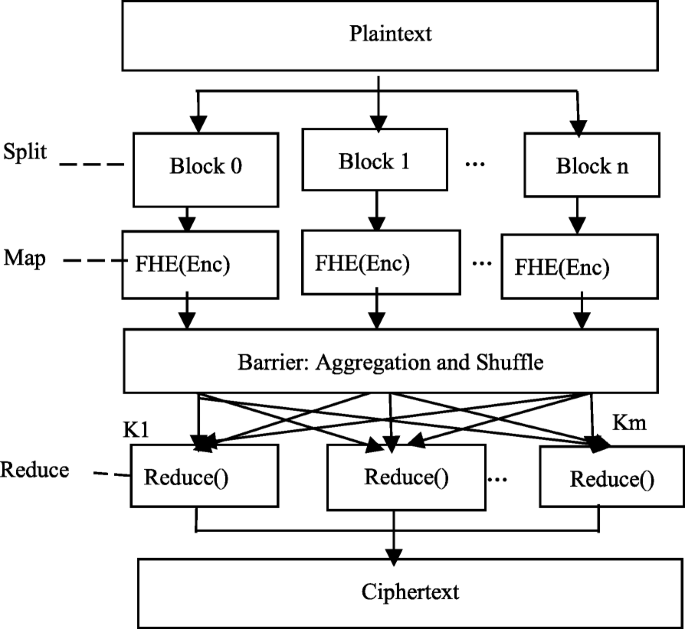
1 Complexity and Performance
One of the biggest drawbacks of homomorphic encryption is that it is computationally intensive and slow. Encrypting, decrypting, and performing operations on ciphertexts requires more resources and time than on plaintexts.However, there are also some disadvantages. Homomorphic encryption can have higher computation times and limited calculation operations, which can impact its efficiency . Additionally, some homomorphic encryption schemes suffer from issues such as extensive memory storage and computing power requirements .
Is ECC or non ECC better : At the cost of a little money and performance, ECC RAM is many times more reliable than non-ECC RAM. And when high-value data is involved, that increase in reliability is almost always going to be worth the small monetary and performance costs. In fact, anytime it is possible to do so, we would recommend using ECC RAM.




